Browser Security issue may Allow Real IP Leak
Published 2015-03-27 11:51 in VPN service
VPN users are facing a massive security flaw as websites can easily see their home IP addresses through WebRTC. The vulnerability is limited to supporting browsers such as Firefox and Chrome, and appears to affect Windows users only. Luckily the security hole is relatively easy to fix.
With a few lines of code websites can make requests to STUN servers and log users’ VPN IP address and the “hidden” home IP address, as well as local network addresses.
The vulnerability affects WebRTC supporting browsers including Firefox and Chrome and appears to be limited to Windows machines.
A demo published on GitHub by developer Daniel Roesler allows people to check if they are affected by the security flaw.
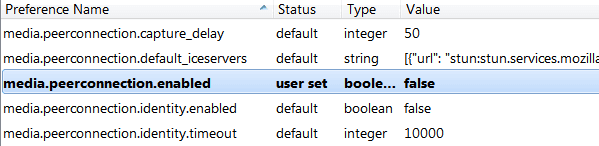
Firefox users should be able to block the request with the NoScript addon. Alternatively, they can type “about:config” in the address bar and set the “media.peerconnection.enabled” setting to false
With a few lines of code websites can make requests to STUN servers and log users’ VPN IP address and the “hidden” home IP address, as well as local network addresses.
The vulnerability affects WebRTC supporting browsers including Firefox and Chrome and appears to be limited to Windows machines.
A demo published on GitHub by developer Daniel Roesler allows people to check if they are affected by the security flaw.
How to fix the WebRTC Security issue
Chrome users can install the WebRTC block extension or ScriptSafe, which both reportedly block the vulnerability.Firefox users should be able to block the request with the NoScript addon. Alternatively, they can type “about:config” in the address bar and set the “media.peerconnection.enabled” setting to false
